Key Takeaways:
- Learn the foundational purpose and functionalities of Intrusion Prevention Systems (IPS).
- Identify different types and functions of IPS and understand how they integrate into cybersecurity frameworks.
- Explore the numerous benefits of implementing IPS in modern organizational settings.
- Gain insights into the importance of maintaining robust cybersecurity through proactive IPS deployment.
Introduction
In our digitally interconnected era, the rapid growth of cyber threats presents significant challenges for organizations across the globe. With cyberattacks intensifying in complexity and frequency, there is an increased urgency for robust security measures to protect sensitive information.
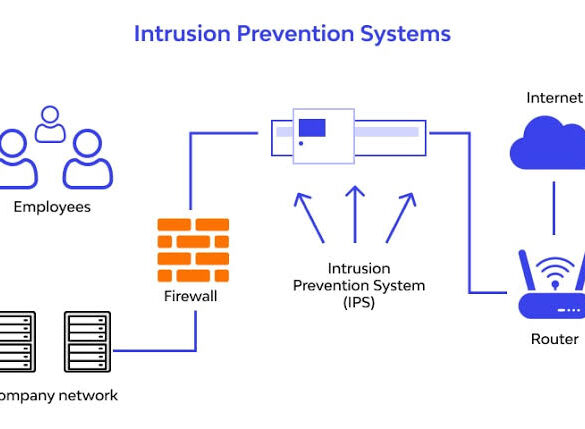
At the core of successful cybersecurity frameworks are Intrusion Prevention Systems (IPS), which are crucial in defending networks against malicious activities. By continuously monitoring and analyzing network traffic, IPS ensures that potential threats are identified and neutralized in real-time, thus fortifying the digital boundaries that protect organizational data.
Understanding Intrusion Prevention Systems
Intrusion Prevention Systems are a critical shield in cybersecurity architecture, providing visibility and proactive defense against unauthorized access. These sophisticated systems are designed to evaluate traffic patterns, deploying advanced algorithms to identify anomalies indicative of cybersecurity threats. Unlike simple detection systems, Intrusion Prevention Systems (IPS) also act to mitigate threats, taking immediate action to thwart potentially harmful network activities.
Operating autonomously, IPS can deliver instantaneous threat intelligence by comparing network activities against established threat signatures and behavioral profiles. This proactive methodology ensures that threats are intercepted at inception, supporting a secure digital environment without constant human intervention.
By maintaining a vigilant watch over the network ecosystem, IPS enhances security and reduces operational costs associated with manual threat management, fostering a highly efficient and effective security posture.
Intrusion Prevention Systems can adapt to evolving threats by continuously updating their signature databases and behavioral models through machine learning and threat intelligence feeds. This allows them to stay ahead of emerging attack vectors, providing real-time protection against even the most sophisticated cyber threats.
Moreover, IPS can integrate seamlessly with other security solutions, such as firewalls and endpoint protection, creating a multi-layered defense strategy that strengthens overall network security. They can also generate detailed logs and alerts, helping security teams monitor network activity and respond to incidents promptly.
As organizations increasingly rely on digital infrastructures, implementing a robust IPS becomes essential for safeguarding sensitive data and maintaining business continuity.
Types and Functions of IPS
Several types of IPS have been developed to address diverse security needs, each serving a specific function within the cybersecurity landscape. The primary variations include Network-Based IPS, Host-Based IPS, and Wireless IPS, each contributing distinct capabilities to an organization’s defense strategy.
1. Network-Based IPS: Strategically placed within the network’s architecture, Network-Based IPS functions as the primary defensive line against external threats.
By closely monitoring inbound and outbound data packets, these systems can swiftly identify and intercept malicious content, preventing potential breaches at the network periphery. They are paramount in defending against many attack vectors that aim to exploit network vulnerabilities and access sensitive data.
2. Host-Based IPS: Deployed directly on individual endpoints, Host-Based IPS provides detailed supervision of system logs, application behaviors, and internal operations.
They are instrumental in detecting and responding to unusual activities within specific devices, offering an extra layer of security against insider threats and targeted malware that bypass perimeter defenses.
3. Wireless IPS: As organizations increasingly rely on wireless communications, ensuring the security of wireless networks has become a priority. Wireless IPS is essential for monitoring the wireless spectrum, identifying rogue devices, and thwarting unauthorized access attempts that could compromise network integrity.
These systems ensure that only legitimate users can access wireless resources, protecting against a unique array of wireless-specific threats.
Integrating these IPS types constructs a comprehensive security infrastructure that protects an organization from external intrusions and internal misconfigurations, safeguarding critical resources and ensuring uninterrupted operations.
Benefits of Implementing IPS
Installing IPS solutions significantly enhances an organization’s defense mechanisms, offering many advantages that bolster cybersecurity resilience and operational efficiency. Foremost, IPS provides unprecedented real-time threat prevention, swiftly responding to and neutralizing threats as they are detected.
This immediate protection is crucial in minimizing vulnerability exposure, safeguarding data integrity, and ensuring business continuity.
Moreover, the automation of threat detection and response protocols inherent in IPS systems alleviates the burden on IT professionals, allowing security teams to concentrate efforts on strategic security initiatives rather than routine monitoring tasks.
By employing data analytics and continuous network activity assessments, IPS yields essential insights into attack trends and emerging threats, empowering organizations to adapt their security strategies proactively.
In addition to operational benefits, IPS meets increasingly complex regulatory compliance demands. IPS safeguards against potential legal repercussions and fines related to non-compliance with data protection laws by automatically mitigating breaches and reducing successful attack incidences.
These systems help maintain stakeholder trust by ensuring the security and confidentiality of sensitive information, cementing an organization’s reputation as a responsible data custodian.
The detailed visibility and analytical reporting IPS provides enable decision-makers to refine security policies methodically, enhancing the organization’s ability to respond promptly and effectively to evolving threats. This proactive defense strategy ensures that organizations remain resilient despite persistent cybersecurity challenges.
Conclusion
In an era characterized by digital transformation and increased connectivity, the threat landscape continually evolves, necessitating equally advanced protective measures. Intrusion Prevention Systems are a pivotal component of cybersecurity frameworks, offering comprehensive protection through real-time monitoring and intervention.
Organizations can defend against cyber threats by adopting IPS solutions and anticipate and adapt to future challenges. This investment in IPS secures sensitive assets and fortifies the foundation for businesses to innovate and grow without compromising cybersecurity.
With IPS as a core facet of their defensive strategy, organizations can confidently navigate the complexities of the digital world, knowing that their cybersecurity measures are robust, responsive, and reliable.